Risk-based vulnerability management
One of the best ways to protect against cyberattacks is to identify and address vulnerabilities before they become critical.
Risk-based vulnerability management is a proactive strategy for addressing vulnerabilities and should be an essential component of any company's overarching security strategy.
Explore risk-based vulnerability management with Trifork Security - find more details below.
vulnerability management
The primary challenge
Mapping a company's attack surface and reducing the overall security exposure by identifying and addressing as many vulnerabilities as possible can be challenging.
The sheer number of potential vulnerabilities, limited resources and an unpredictable and dynamic threat landscape pose obstacles even for the most dedicated IT specialists. They often spend (too much) time on vulnerabilities that may never be exploited, while potentially overlooking critical vulnerabilities that could expose a company to unnecessary risks.
This is where risk-based vulnerability management comes into play.


Risk-based vulnerability management
Identify. Evaluate. Prioritize. Manage.
Risk-based vulnerability management differs from traditional vulnerability management by adopting a holistic approach to vulnerability handling. Through automatically generated risk models, potential threats are identified and evaluated in relation to the risk they pose to a given company.
This contextualization allows vulnerabilities to be prioritized based on severity and risk level, ensuring that the most critical vulnerabilities are addressed first.
This approach helps companies allocate their resources more effectively by focusing on vulnerabilities that present the greatest immediate risk.


presenting tenable
RBVM with Trifork Security
Trifork Security is a partner with Tenable®, a leading player in all types of vulnerability management.
Around 40,000 companies utilize Tenable's Cyber Exposure platform daily to understand and mitigate cyber risks. The platform provides a unique insight into the risks across the modern attack surface.
At Trifork Security, we specialize in Tenable. We work with the full product portfolio and are one of only three Danish companies with Gold Partner status in Tenables partner program Assure. We have delivered numerous Tenable solutions to both public and private companies in Denmark, including one of the largest Tenable installations in Scandinavia.
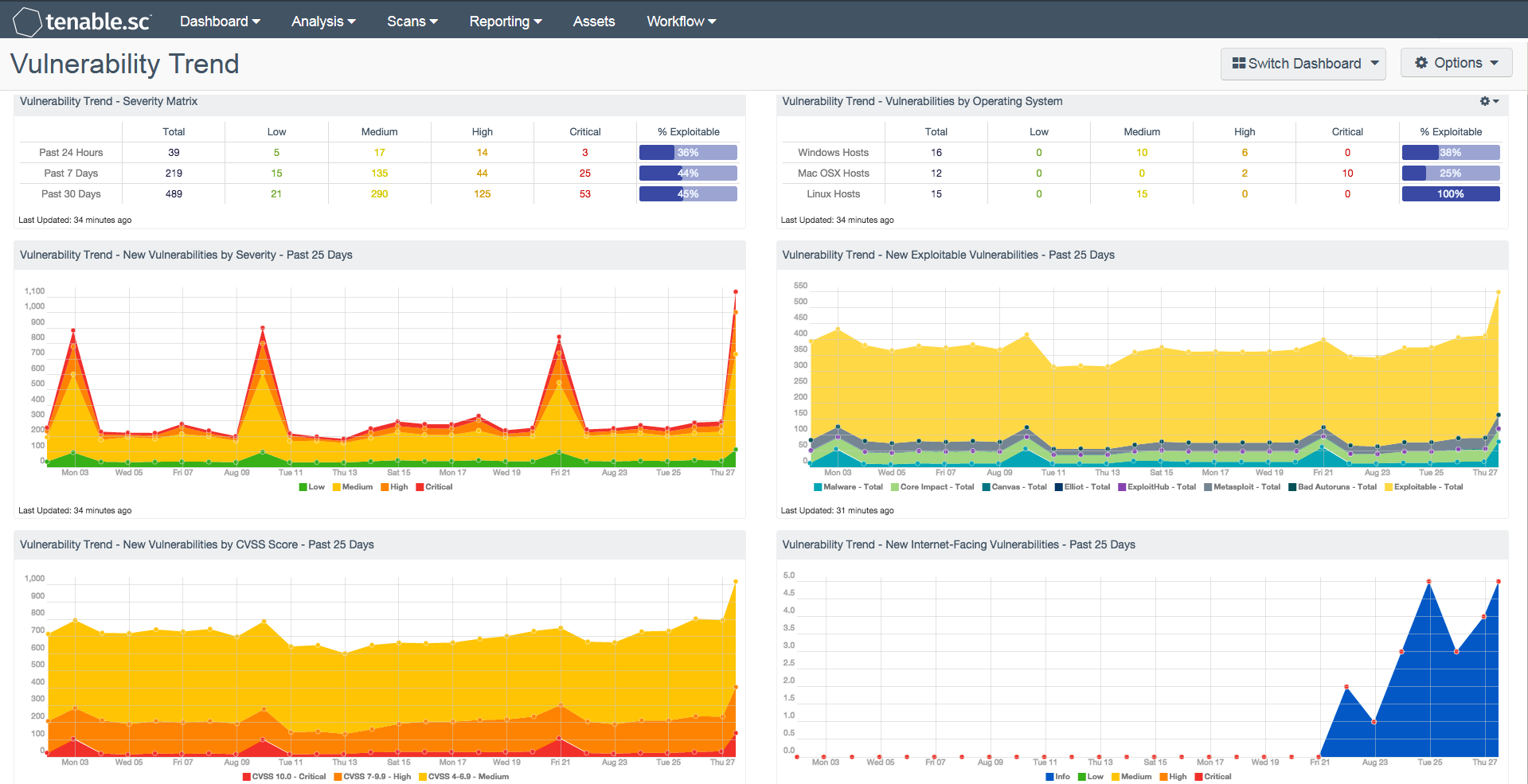

Strengthen your network and effectively safeguard devices against attacks.
Prioritize vulnerabilities based on a risk-based approach.
Gain insights into your vulnerabilities and other measures over time.
Obtain an overview of your environment and identify potential unknown devices.
Integrate vulnerability management with existing processes seamlessly.
Generate valuable feedback with recommended solutions to address issues.
Contact